Let's break down crypto wallets. Learn about the various types available. Check out how they function. Decide which one would suit you best.
Key Points to Remember:
- Crypto wallets don't literally hold digital money. It's not like your real wallet.
- What they do hold are keys. These keys are for buying cryptocurrencies. They also sign off all transactions.
- Physical devices, software, and paper each can serve as crypto wallets.
- Your trading requirements will guide you to the best crypto wallet.
What Is a Crypto Wallet?
Picture this: you've got an awesome keychain. It's got your public and private keys. These keys are your passport to managing your crypto balances. They pave the way for your journey in the crypto galaxy. They help you send and receive cryptocurrencies. Some even let you buy and sell crypto or use decentralized apps (dapps).
Don't think that you're passing digital coins from your phone to someone else's. That's not how it works. Instead, your private key autographs your transaction. The transaction is then announced loud and clear to the blockchain network. Your account and the receiver's account get updated to show the new balances.
The term 'wallet' can be tricky. It doesn't pocket cryptocurrencies like your wallet pockets cash. Its job is more of reading a list, a public ledger. It tells you how much balance you have. It also keeps those private keys you need to go on your crypto adventures.
What are Public and Private Keys?
You will always get a key when you have a crypto wallet. There are 2 different types of crypto keys:
- Public Key: is like a bank account number you can share with others.
- Private Key: is like a secret password or PIN, never share it with anyone!
These keys are pivotal in public-key cryptography. They work together to encrypt and decrypt data, securing communication and transactions.
Why a Crypto Wallet Is Important
Storing crypto on an exchange might be tempting, but it isn't wise, except for small amounts meant for trading. It's better to keep most of your crypto safe in a wallet. You'll have two options here:
- Hot wallet: connected to the internet; easy access and flexibility, but less secure.
- Cold wallet: not connected to the internet, more secure, but less accessible.
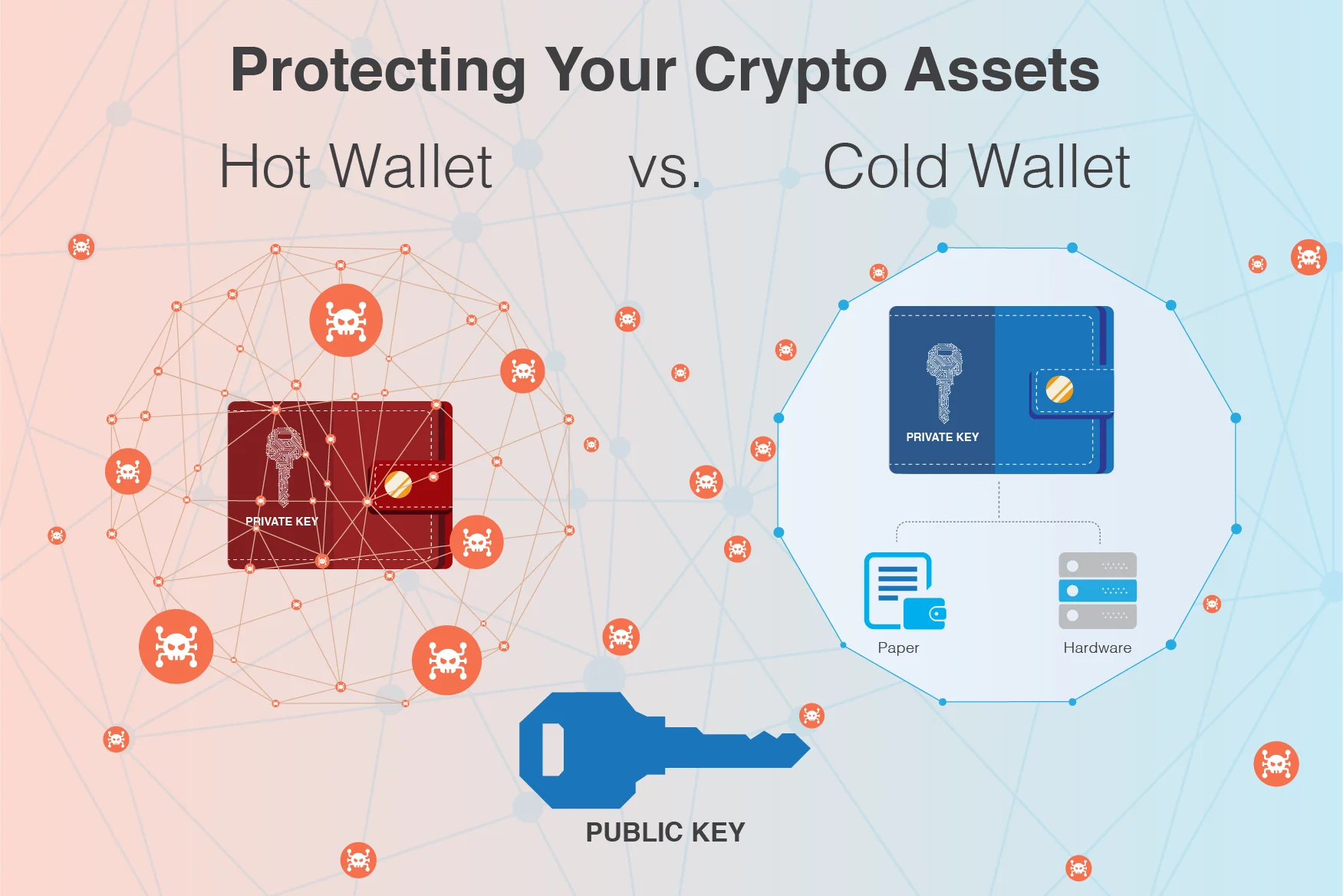
With a wallet, you're in charge of your private keys and money. Full power and control are in your hands.
How Do Crypto Wallets Work?
Contrary to what it sounds like, wallets don't hold coins directly. Instead, they hold the keys for your coins, which are stored on public blockchain networks. To perform transactions and access your crypto, you'll need to do the following:
- Verify your address using private keys made of unique alphanumeric codes.
- Use your public key when receiving funds from others.
- Keep your private key secure and never share it with anyone.
The speed and security of transactions often depend on the type of wallet you have. Hot wallets provide faster access and user-friendly interfaces, but with lower security due to their internet connectivity. On the other hand, cold wallets offer maximum security of your coins, as they are not connected to the web, but accessing and using them might require extra steps. How to use MetaMask: A step-by-step guide - here.
Remember, it's crucial to manage your keys wisely and choose the wallet type that best suits your needs. That way, you can enjoy the benefits of cryptocurrencies while staying safe and in control of your assets.
Hot and Cold Crypto Wallets

There are two types of crypto wallets Based on its flexibility. You've got your hot wallets. You've got your cold wallets. They're like polar opposites. Now, Let’s learn the differences:
Hot Wallets
Hot wallets are like a mini bank in your pocket. Yep, they're always online, tapped into the web. This makes them easy to access, but also an easy target for cyber thieves.
These are what hot wallets look like:
- Web Wallets.
- Desktop Wallets.
- Mobile Wallets.
In these wallets, mystical things called private keys are stored. They're like a secret code to your treasure. They live on the wallet's app, which is always online. But, be cautious! Connected to the internet, they're vulnerable to sneaky hackers. Don't keep all your treasure in one place!
In the web world, you can't trust everything. There are traps set by cyber thieves - they're called vulnerabilities. They aim to steal your private keys. Always prefer a hot wallet that has good security with strong encryption.
But Why Use Hot Wallets?
So, you ask, why use hot wallets if they're risky? Good question! The answer is convenience. Want to do transactions quickly and frequently? Use hot wallets. But remember to use a mix of hot and cold wallets for better security.
Cold Wallets
Now, what about cold wallets? They're like a safety deposit box. Totally offline. No internet, no hackers. But not as handy as hot wallets. Ever seen a secret message written on a piece of paper? It's kinda like that.

The two most popular types of cold wallets include hardware and paper wallets
Check out these cold wallet examples:
- Paper Wallets.
- Hardware Wallets.
Paper Wallets
Now, you might wonder, what is a paper wallet? It's a place where you scribble down your private and public keys. Phishing attacks cannot get to them. It's safer, sort of like locking your treasure away.
But ain't nothing perfect, right? Imagine you lose that piece of paper or it gets destroyed. It's like losing a map to your treasure: irreversible loss. So, balance is key, use a mix of both wallet types.
Hardware Wallet
You can think of it as a techy pocketbook. It's typically a gadget that can connect to your computer via USB or Bluetooth. This little helper stores your all-important keys, kind of like a digital locksmith. To sign a transaction, it needs your touch. You literally have to push its button. This geeky feature does wonders for security because it stops sneaky hackers in their tracks!
Now, let's say you've got a chunk of cryptocurrencies, like Bitcoin or Ethereum. Think of it as your modern treasure. You won't need it right away, so how do you keep it safe? You tuck it away in a cold wallet. Think of it as a super-secure piggy bank stored offline. But remember, with great power comes great responsibility! You have to look after your treasure - don't lose it or let someone swipe it.
Hold up, before you start, here's a pro tip! For an extra layer of security, why not hide your public and private keys in different spots? Keep them offline and tucked away in safe places. Your physical wallet? That might be well-kept in a trusted safe deposit box.
Hot Wallets vs Cold Wallets: Which Are Better?
Well, it depends on what you need. Imagine you're a modern-day trader, trading crypto every day. For you, quick access to your digital coins is crucial. That’s where the hot wallet comes in handy - it's worth considering.
But what if you have tons of cryptos and security is your top priority?
You can't beat the convenience of a cold wallet. It might require more hands-on attention, but it's a solid fortress for storing your crypto assets.
Think safety deposit box, but for your digital treasures.
Custodial and Non-Custodial Wallets
Wallets can also be divided into custodial and non-custodial types in addition to the categories stated above.
| Criteria | Custodial Wallets | Non-custodial Wallets |
| Access to Funds | Private keys are in control of the wallet provider, thereby implying that they also have control over the user's funds. | Only the user has complete control and access to their private keys and the funds associated with them. |
| Recovery of Funds | Easy options for recovery in the event of losing access to login credentials for the wallet. | Impossible to recover funds in non-custodial wallets after losing private keys or recovery phrases. |
| Security | Connection to the internet makes Custodial wallets vulnerable to hackers. | Without any internet connection, non-custodial wallets are secure from cyber threats. However, users should ensure secure storage of private keys and recovery phrases. |
| Creating Accounts | Lengthy KYC and AML procedures lead to a complicated process for creating accounts. | No KYC and AML procedures with straightforward and fast account creation. |
| User-Friendliness | More user-friendly with interactive interfaces. | Technical know-how required for using non-custodial wallets reduces user-friendliness. |
Custodial Wallets
Usually, web-based crypto wallets are custodial. Found on cryptocurrency exchanges, these wallets offer convenience and ease. They're popular with beginners and experienced traders.
Custodial wallets have one main difference from others: users don't control their tokens fully. The exchange holds private keys for transactions.
Trust in Security
Users must trust the provider for secure token storage. Strong security measures are a must. These include email confirmation, two-factor authentication (2FA), and biometric login like facial recognition or fingerprint verification. Transactions can't happen without proper security setup.
Further Steps for Safety
Exchanges and custodial wallet providers work hard to protect tokens. For example, some funds are transferred to a cold wallet, away from online attackers.
Crypto.com's Security Measures
Crypto.com has taken many steps to protect customers. After thorough security audits, Crypto.com became the world's first crypto company with ISO/IEC 27701:2019, ISO22301:2019, ISO27001:2013, and PCI:DSS 3.2.1, Level 1 compliance. It was independently assessed at Tier 4, the highest level for NIST Cybersecurity and Privacy Frameworks, as well as Service Organization Control (SOC) 2 compliance.
Insurance for Customer Funds
The company also has US$360 million of insurance protection for customer funds.
Non-Custodial Wallets
These are cool tools that let you control all of your own money. You see, your secret key is stored with you, not somewhere else.
You write down 12 random words, known as a 'recovery' phrase. It's unique to you. Just like a top secret password of sorts! Those words? They create your wallet's keys. This phrase is your plan B, in case you lose your device.
What happens if someone else gets that phrase? They control your wallet. It's like they stole your keys! If you lose that phrase, you lose your access to your money. So, guard it well!
No digital copies, no prints at public places, or photos.
Hardware and and DeFi Wallet Belong To This
It is the same as hardware wallets. These are non-custodial, with keys stored inside the device.
And before I forget, there's the Crypto.com DeFi Wallet too! It's a software-based, non-custodial wallet. The point is, with these wallets, you're always in control. As they say, 'not your keys, not your coins!' It's all yours!
Now, here's the catch. You have to manage your own security. You've got to keep those passwords and seed phrases safe! If they're lost, you're in trouble. It's hard or potentially impossible for anyone to help you recover them, since backups don't exist on servers anywhere.
That's non-custodial wallets in a nutshell. They give you freedom, but remember, with great freedom, comes great responsibility!
Custodial vs Non-Custodial – Which one Better?
Deciding between custodial and non-custodial wallets? Let's weigh their perks and downsides.
Custodial Wallets: Safer for the Forgetful
- If you often misplace passwords or devices, go for a custodial wallet.
- An exchange or custodian will take care of your wallet and provide better security backup options.
- They're popular amongst beginners with lil' crypto trading experience.
- Transaction fees can be cheaper or even free.
Non-Custodial Wallets: Total Control
- If you're a control freak about your funds, choose a non-custodial wallet.
Remember, it's all about what works best for you.
Multi-Signature Wallets for Extra Safety
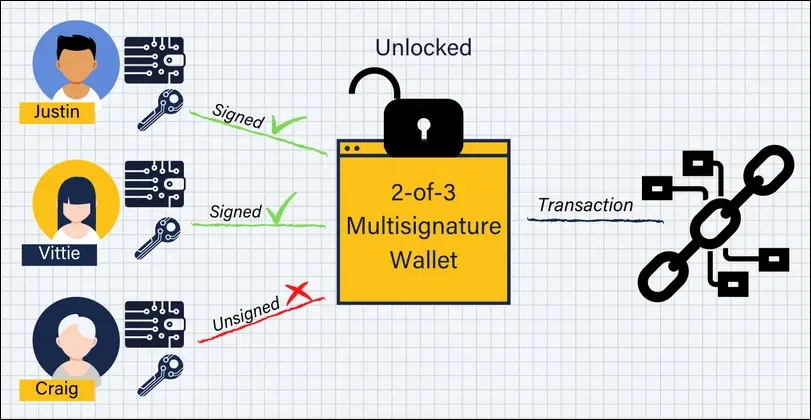
Justin, Vittie, and Craig possess the three keys required to open the multisig wallet
Multisig wallets need at least two private key signatures to approve transactions. They're handy in a few scenarios:
- You can avoid losing complete wallet access if you misplace one key, since there are other keys to sign transactions.
- They help prevent fund misuse and fraud, perfect for hedge funds, exchanges, and businesses. Since each key-holder needs to agree on transactions, no one can act alone.
These multisig wallet versions exist across the board—hot, cold, hardware—you name it.
So, think about your needs, your habits, and your crypto goals. Then, pick the wallet that suits you like a glove. Good luck and happy crypto-ing!
NFT Wallets
An NFT wallet serves as a safe house for your non-fungible tokens (NFTs). You can pick from hardware wallets or software-based wallets - your call.
How to use MetaMask: A step-by-step guide
Choosing the Right NFT Wallet
Your ideal NFT wallet rests on several things. How savvy are you with such things? Which security measures do you need? What types of NFTs are you aiming to stockpile? Keep these in mind when picking out an NFT wallet:
- Compatibility - Do you need a wallet that plays nice with the NFT marketplaces of your choice? Look out for this.
- Quality Security - Look for key security measures like email confirmation, two-factor authentication (2FA), or even biometric login.
- Simple and Sleek - A good NFT wallet should be a breeze to use and set up.
- Accessible Via Various Devices - Many NFT wallets are accessible from network extensions or mobile/desktop applications. For more comfort, pick a wallet available on several devices that also syncs real-time transactions.
- Friendly with Other Networks - Any wallet can support Ethereum-based tokens. But if you plan to mint, buy, and sell tokens on other networks, you'll need a compatible wallet.
Some popular hardware wallets are Ledger and Trezor. But keep in mind, neither support NFTs natively. To store and manage NFTs, you'll need to hitch up your hardware wallet to a capable hot wallet.
Crypto.com DeFi Wallet
Crypto.com DeFi Wallet is special. And it's non-custodial!
Users keep control of private keys and assets. Use it on Android or iOS. Manage 700-plus tokens across 20-plus blockchains. Send crypto anywhere, choosing speed and fee.
It supports NFTs on Cronos, Ethereum, and Crypto.org Chain. View top collections easily with NFT Spotlight! Want passive income? Lock up cryptocurrencies like USDC, CRO, and DOT. Manage NFTs in the Crypto.com App too!
Takeaway - Choosing the Right Wallet
Crypto wallets differ. No perfect solution exists. Each wallet type has strengths, purposes, trade-offs. Users decide what's best.
Risky users, making regular, quick online payments? A hot wallet like Crypto.com App may work. A bit risk-averse? Planning to hold coins long term? A secure offline device, like hardware wallets, might suit better.
The final choice is up to you. I personally use non-custodial Crypto.com DeFi Wallet for as a secure option. Anyway, storing many coins in one wallet is risky. A mix of cold and hot wallets is ideal, balancing convenience and security.
FAQ
Should Beginners Use a Custodial or Non-Custodial Wallet?
Custodial wallets need trust. Providers store your crypto. Non-custodial wallets give you full control. You store private keys. Beginners may like custodial wallets because they're easy. Experts often prefer non-custodial wallets.
What Makes Crypto.com DeFi Wallet a Great Option for Beginners?
Crypto.com DeFi Wallet is a non-custodial wallet. It lets you control private keys and assets. Supports 700+ tokens and 20+ blockchains. You can pick transaction speed, fees, and manage NFTs. Plus, you can earn passive income through staking
How Do Hot Wallets Differ from Cold Wallets?
Hot wallets connect to the internet. They're useful for regular transactions, but can be hacked.
Cold wallets are offline, which makes them safe. But, they may require extra steps. It's vital for beginners to learn these differences.
What are the Risks Involved in Using a Hot Wallet?
Hot wallets can be hacked online. So, users need strong encryption, two-factor authentication (2FA), biometric authentication, and secure login credentials.


 12 mins read
12 mins read